
5 Problems Businesses Encounter When Developing Online Training Platforms
The path to developing an online training platform is not easy, to achieve success there will certainly be problems and risks that businesses need to pay attention to. Don’t worry too much! Check out the following 5 problems that your business may be facing.
5 things to consider now if your online training business is not working:
1. Low ROI
ROI (abbreviation of Return On Investment) means return on investment, return on investment or also known as profit rate. This is an index that helps businesses measure the performance or profit from an initial investment.
This is a problem that many online course content developers worry about in the early stages. When investing a lot in creating content, personnel costs, operations, software, etc. But when collecting, the profit is too low, there are no students registering for the course.

This is an index that directly affects the business’s profits, so businesses pay attention to finding solutions to improve the problem of low ROI. Some businesses do not build a brand but want to generate revenue immediately, so they invest a lot of money in advertising, but the results are very low. Advertising costs account for 80% of revenue.
If your business is experiencing this situation, stop and consider the following factors:
Data Analysis:
is the key to evaluating and improving the effectiveness of course content. By collecting and analyzing data from many different sources, we can objectively evaluate the effectiveness of each course. From there, we can determine which factors are affecting the learning outcomes of students, such as content quality, teaching methods or interactions between instructors and students.

Improve Content:
Course content plays an important role in retaining students. It is the core issue for students to continue investing in the course and recommend it to others. To improve the quality of content, make sure the courses are constantly updated and suitable for the actual needs of students.
In addition to teaching theories, applying different teaching methods to make learning practical such as solving case studies, practice, and interaction between lecturers and students is necessary.
Strengthen Marketing:
To attract more students, we need to diversify marketing channels, such as social networks, email marketing, online advertising. Besides, building a strong personal brand, providing valuable free content is also a way to attract the attention of potential customers.
Ensure Market Demand:
Before mapping out the curriculum, carefully research the market to understand how much % of market demand this course is providing, what are the gaps that other courses cannot meet. Nowadays, each short-term or long-term course is awarded a certificate after the course, this is a good way that businesses can apply to motivate students to complete the entire online course and have results to beautify their profile.
2. Poor video quality
Many courses fail because their content is not up to par with what learners are used to. Modules may be too large and not engaging for viewers during online training. Some problems encountered include:
High content loading delay: When videos or content are delivered in large chunks, loading times can be long, especially for users with unstable and slow network connections.
Disrupted experience: Users often experience lag or long waits to view full content, which reduces the learning experience.
Not only that, it is also difficult for administrators to manage online training data, a large volume also makes the server heavy and difficult to download for data analysis.
Design and test carefully
Designers can help you solve this problem, they help you present information logically, in attractive formats, with diverse presentations, combined games, etc. They also know how to arrange content into small modules that readers can easily absorb.
The main solution to the problem is to divide the content into shorter segments. This helps the loading speed to be significantly improved, users do not have to wait for the entire data file
Reduce lag, short segments allow for smoother management and transmission of teaching content, the network does not necessarily have to be too strong to be able to download or view smoothly on the website.
Buy Thu Do Multimedia’s CDN solution now – The leading solution to accelerate digital content transmission
With the strong development of online content, especially video streaming, applying CDN solutions not only improves content quality but also enhances user experience.
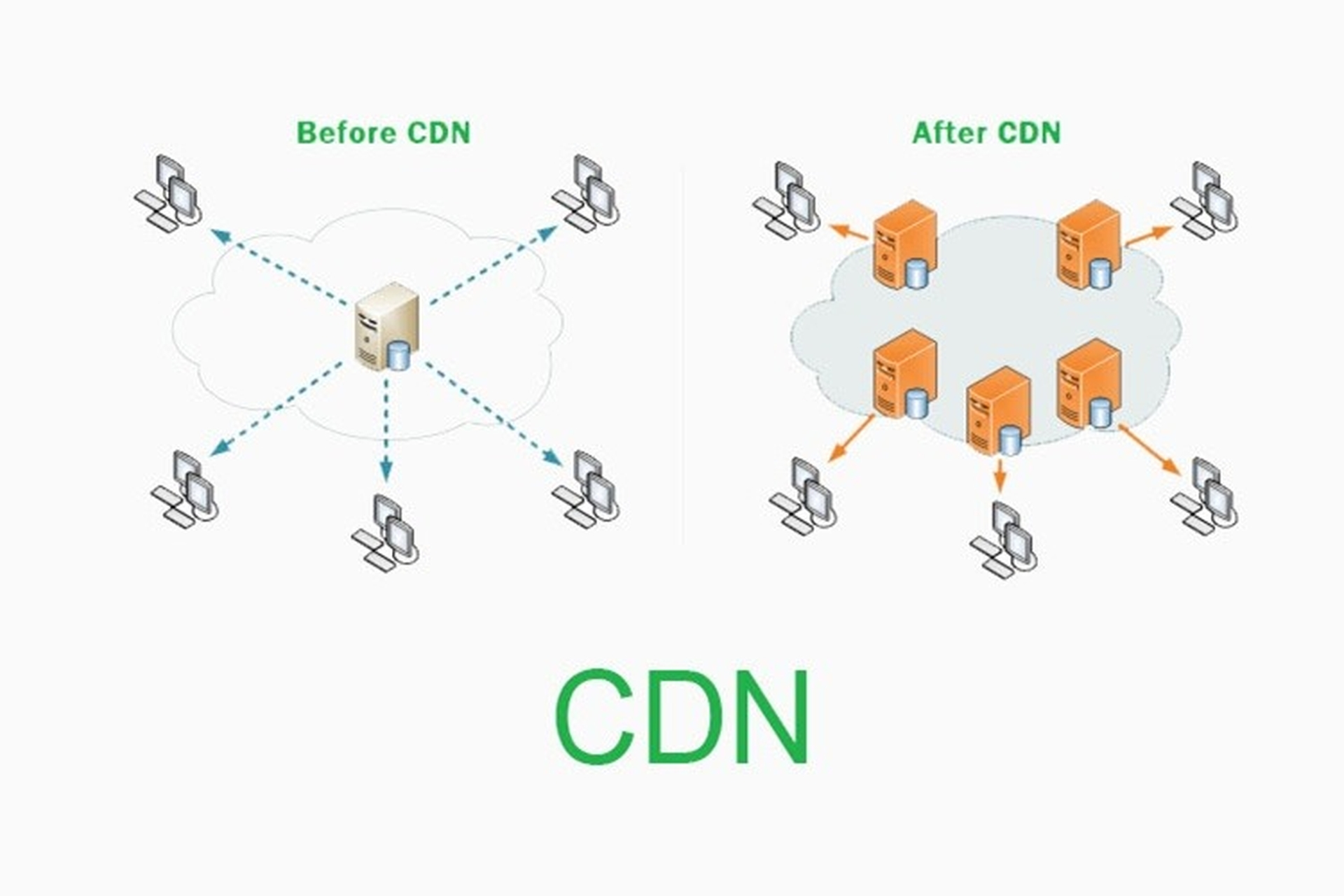
Deliver content closest to users: CDN stores copies of content on multiple servers in different geographical locations, from which content is delivered from the server closest to the user, reducing loading time. This is especially necessary for multinational online training businesses, because the fastest CDN delivery is needed to provide a great experience for learners.
Optimize bandwidth and transmission speed: By cutting content into small pieces and transmitting it through the CDN network, the loading speed and content quality are significantly improved, minimizing lag and interference no matter where learners are.
Ensure content quality in all conditions: Even with a large number of visitors, the CDN system is still able to maintain content quality thanks to the ability to distribute the load evenly across servers.
Small investment – Unexpected efficiency
CDN is truly a necessary solution in today’s video industry. Without knowing about CDN, businesses will not be able to bring a smooth learning experience to subscribers. Online platforms always try to squeeze the video resolution down, making the video very blurry and less interactive. This is a big problem and CDN helps businesses to deliver scientific online content, in line with the learner’s psychology and sharp and smooth in any situation.
A small investment but can help businesses convey messages seamlessly, keeping viewers engaged for a long time. It’s like the experience of watching a good movie on “Netflix”, very smooth and very engaging. Increase learning efficiency for students.
3. Ineffective Marketing
You have a product, but is your business doing a good job of marketing to convey the message to customers? Among hundreds of thousands of online training platforms, what makes you stand out the most? This is a difficult question, right?
Marketing an online course properly is an important factor in determining the success of the course. It provides information to the target audience and encourages them to quickly make a decision to “experience” the course. However, even if you have created a high-quality, informative course, it will not be well communicated to the right people.
For example, the Duolingo learning application is a typical case study for “a separate path” in the online training industry. They accurately identify customers as the young, dynamic, fun, humorous generation, learning like playing, playing like learning, so the marketing sentences or reminders to learn of Duolingo app are very cute and true to the learner’s insight, “I’m too lazy to study”, “I miss you so much, let’s go back to studying”, .. Help retain customers and spread quickly.

How to increase marketing like Duolingo
Identify the right target audience: Analyze customers according to factors such as age, interests, location, habits, desires, .. To adjust marketing messages to suit the needs of each audience. For example, with primary school students, online training teachers should incorporate many thinking and entertaining games into the lecture, so that children are easily stimulated and explore more.
Create engaging learning content: divide online training content into different pillars, such as blogs, seminars, games, exams, in-depth, etc. Take advantage of technology in teaching to show the intuitiveness and practicality of the theory being received.
Reach the right place: Popular channels used to reach target customers in online training platforms such as social networks, email marketing, websites, groups, etc. In particular, the website needs to be optimized (SEO) properly, trying to bring the article to the top of Google to make it easier for learners to access. In addition, businesses can send marketing emails directly to subscribers to encourage them to buy or re-register for many different courses. This is a channel that Duolingo does very well.
4. Security issues in online training
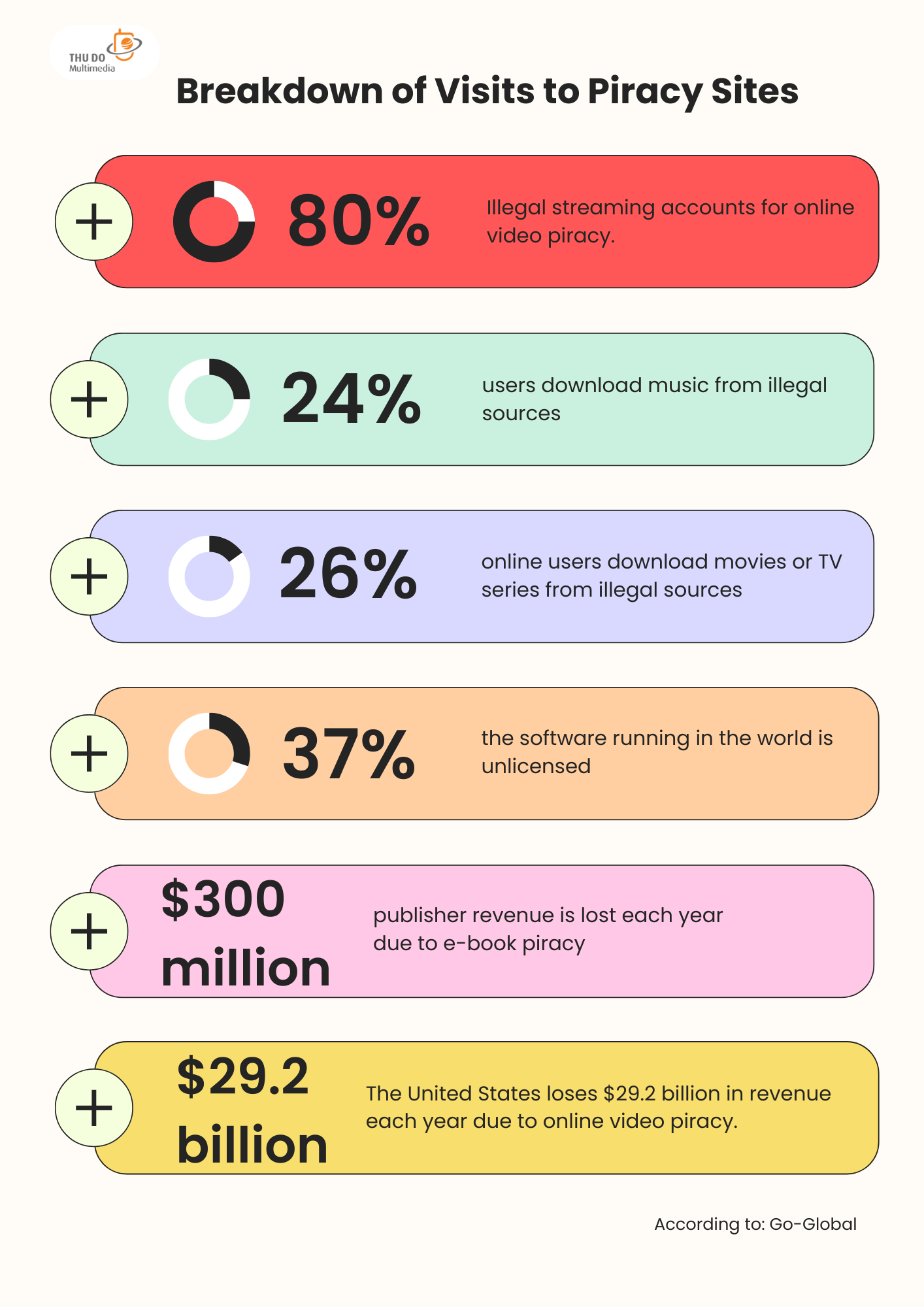
According to Go-Global’s report on “online copyright infringement”, more than 80% of online video copyright infringement occurs“. This number is alarming, isn’t it? Online courses are also among the videos that hackers often steal.
Online course piracy is a problem that businesses may not have thought about when they encounter a situation of “unsold customers” despite “good courses”. Businesses do not know that their courses have been distributed and “commercialized” at a value of only 1/10 of the original price that the business is selling.
Every day, hundreds of courses are released, but there are also hundreds of courses that are blatantly stolen. Pirated websites will aggregate all the courses of online training platforms or influential teachers and “sell” them at an unimaginably low price. As a result, the assets of the business are reused without their knowledge, and their own original courses have no revenue.
Read more: How Sigma DRM Can Be the Game-Changer for Online Course Management in 2025
Another security issue is the leakage of personal data of students. Information such as name, address, phone number, email can be stolen and used for malicious purposes. In addition, unauthorized access to learning materials, lectures, and tests is also a major concern. Cyber attacks such as DDoS attacks, malware, and viruses are also frequent threats to the online learning system.
A short-sighted mindset of the leader is that: online courses of small businesses do not need copyright protection because there will be no hackers to attack. But the truth is, every course is a “fat prey” for pirated websites to attack. And once a method of protecting assets in cyberspace is not found, the business will lose revenue in the long run.
Security solution – copyright protection for online courses at Thu Do Multimedia
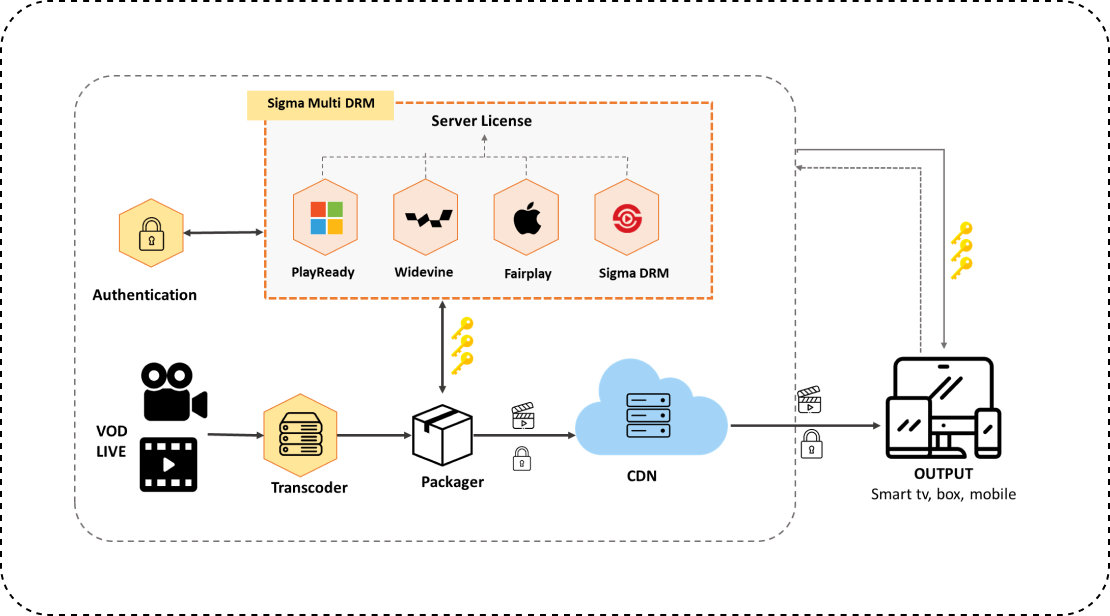
Thu Do Multimedia has developed Sigma DRM technology with the mission of helping businesses protect digital copyrights in cyberspace, reducing the rampant copyright infringement today.
Simply put, Sigma DRM works by encrypting file content with a secret key. When students need to use the online course file, they need the Key to decrypt the file. At this point, students can access the course and enjoy the full lecture in a private space.
Multi-layer content encryption, comprehensive protection:
Overcoming all barriers:
Sigma DRM uses multiple layers of complex encryption, turning learning content into an “impregnable fortress of attackers”. This helps prevent all forms of unauthorized copying and sharing, ensuring that only authorized people can access and use the documents.
Absolute peace of mind:
With a solid security layer, educational institutions can rest assured that their learning materials are securely protected, avoiding leaks or unauthorized use.
Flexible access management, meeting all needs:
Detailed authorization:
Sigma DRM allows administrators to set different access rights for each type of document and each user group. For example, teachers can access all documents, while students can only access documents related to their course.
Optimize the learning experience:
Flexible authorization helps ensure that each user only has access to the necessary information, avoiding information overload and improving learning efficiency.
Effectively detect and prevent copyright infringement:
Monitor all behaviors:
Sigma DRM’s system continuously monitors all activities related to learning materials, from downloading, sharing to printing.
Fast handling of violations:
When detecting any copyright infringement, the system will automatically warn and lock the user’s account, helping to protect the rights of the creator.

In short, Sigma DRM is a comprehensive security solution that helps educational institutions protect learning materials, prevent copyright infringement and create a safe and professional online learning environment.
Thu Do Multimedia’s new partner in the education sector is the moon.vn platform, a large online education website in Vietnam. Specializing in providing courses for high school students, university entrance exam preparation.
When deploying Sigma DRM, moon.vn courses are protected and managed easily. No longer is the situation where 60% of courses were stolen before, but instead 100% of courses are managed for access rights, helping businesses increase their reputation and security, increase revenue and profit from online training courses.
Education is the field that needs to deploy Sigma DRM first, because the need is not only to protect digital products such as online courses but also to protect important online documents of teachers, personal information of students, etc.
Protect to survive
Businesses have spent a lot of effort and money to create and own online courses, so the factor of “copyright protection” to avoid attacks or blatant infringement is the first and most important thing in maintaining a long-term business.
The cost of implementing Sima DRM is really too small compared to the loss of revenue that businesses have to bear when courses are leaked. This has been verified.
If your business is experiencing this loss, please contact Thu Do Multimedia – the leading business in online copyright protection in Vietnam, to be listened to, have your difficulties resolved and receive the most thoughtful advice on the optimal solution for your business.
5. Poor resources/unfinished products
This is the final reason for the damage that businesses can most likely encounter in the online course business. Once the course has good content, learners are easily bored, uninterested and do not see the value of the course and negatively affect the brand.
It is necessary to conduct an evaluation survey to know the current state of the training quality, how learners feel about the course, what are the desires and needs for further improvement of each course? From there, businesses will optimize the course and produce more valuable and useful lectures.
Suppose you are developing an online course on digital marketing. After completing a module on SEO, you can conduct a survey to assess learners’ satisfaction with the content, presentation and practice exercises. Based on the survey results, you can adjust the content, add more real-life examples, or change the presentation to better suit the needs of the learners.
Sigma DRM I mentioned above can help businesses save a lot of time, because this technology will analyze each customer experience in detail and suggest better ways to handle the course. This helps businesses not to focus on expensive surveys, but only focus on improving each point in the analysis data is best.
Big challenges come with big rewards…
It’s often difficult to get into a business like eLearning because the risks are often high. However, if you play your cards right, it can be a very profitable venture. The risks of developing online training that we describe in this article may be real for industry professionals, but with careful planning, they overcome them every day and achieve their goals. You can do the same by conducting pre-launch due diligence and setting up a few rounds of testing.
The business’s job now is to pick up the phone and contact Thu Do Multimedia for advice on useful solutions such as Sigma DRM and Sigma Multi CDN – these are 2 warriors that help businesses “fly high and far” on the path to conquering online courses. Get rid of online course content theft easily and manage your business’ digital assets with ease.


























Recent Comments